Top 5 Tips to Incorporate Cybersecurity into Your HRIS
Cybersecurity is a prevalent issue that has received an increased attention in various organizations lately. It is to no surprise for us since it has continuously become a hot topic brought to the spotlight by the significant data breaches in the past few years which happened even in Singapore.
With benefits such as lower investment cost, automatic system updates and backup, freedom to work from anywhere anytime, many companies are switching to cloud computing especially on cloud HR system. The advent of the cloud has created significant changes to organization in the past few years. Although it brought lots of benefits, companies are still hesitant to move their data to cloud which mainly because of security concerns.
The recent cyber-attacks waged against HR data services firm ComplyRight and talent management platform PageUp prove how employee data remain vulnerable to identity theft even in the era of stricter data privacy rules. The mere existence of such data creates risk, companies that store sensitive employment information – whether through a third-party service or an in-house HR information system (HRIS) – become the prized target of cybercriminals. By gaining access to employee names, birthdates, social security numbers, salaries, and bank details through HR documents, data thieves can proceed with a number of other system hacks.
In Singapore itself, one of the most recent and the worst cyber-attack happened in Singapore on July 2018 is the hackers infiltrated the databases of Singapore Health Services (SingHealth), a total of 1.5 million SingHealth patients’ non-medical personal data were stolen, while 160,000 of those had their dispensed medicines’ records taken too. This incident once again has bought the public attention on the internet security.
How can HR departments ensure their HRIS is safe from hackers?
At the start of HRIS software implementation, HR and IT managers need to ensure the nature (and coverage) of security measures the software vendor will put in place is sufficient for the size and complexity of the organization. The data management system will also need to comply with the Personal Data Protection Act (PDPA) of Singapore.
For HR teams that rely on HRIS vendor for its cloud hosting services, it is important to check that the service provider not only implements a robust security system) but also complies with PDPA rules on how and where to store personal data and but also ISO security policies.
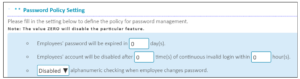
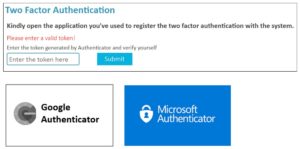
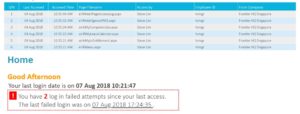
Below are the other five tips you may consider: –